Authentication
The LS One API uses token-based authentication via a JWT token. This allows for secured access to LS One resources without requiring user credentials as long as the access token is valid and not expired.
An LS One user with the user permissions to access the API can login with the following call:
POST /api/authorize/authenticate
{
"userName": "admin",
"password": "12345"
}On succesful authentication the API returns a short lived JWT access token that expires after 20 minutes and a refresh token in a HTTP-only cookie that expires after 24 hours.
In the following calls to the API the client must send the JWT token in the Authorization header when requesting protected resources from LS One API.
#Response headers
access-control-allow-origin: *
content-type: application/json;
charset=utf-8
{
"token": "{authentication_token}"
}If the authentication token expired the client will receive error 401 - Unauthorized and will be able to refresh his or hers autentication token using the refresh token received at the time of authentication.
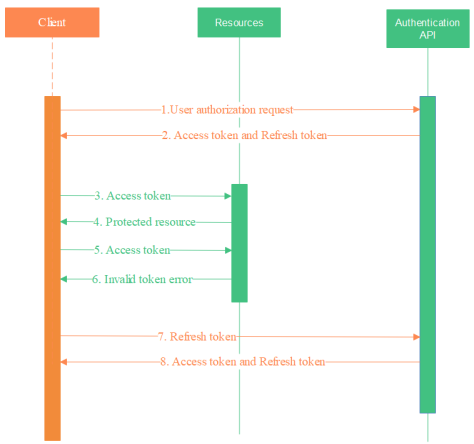
LS One API provides several configurable settings related to JWT tokens, see Configuration.
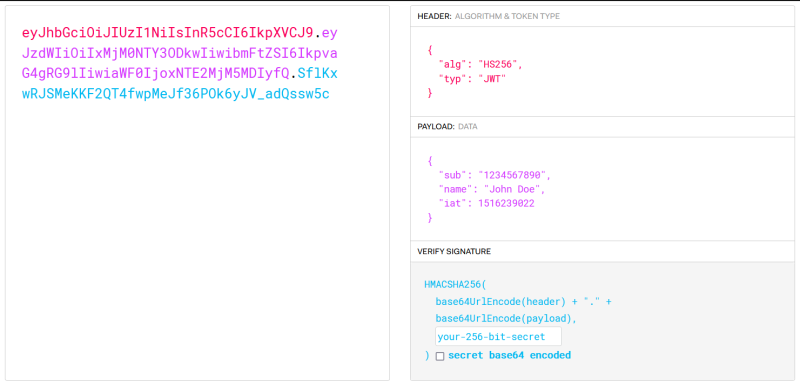
JWT Token Internals
JWT stands for JSON Web Token and provides a stateless way of authorization and information exchange.
It's basically a long encoded string containing three parts separated by dots, each part being Base64 encoded. These parts are:
-
Header: contains metadata about the type of token and the cryptographic algorithms used to secure its content
-
Payload (set of claims): contains verificable security statements, such as the identity of the user and the permissions they are allowed
-
Signature: used to validate that the token is trustworthy and has not been tampered with

JWT is a signed token (using secret or public/private key pair) and not an ecrypted one. Therefore, even though JWT can verify the integrity of the claims contained within it, it cannot hide that information
A typical JWT looks like this: